BurpMCP
STDIOHTTP-SSE通过MCP将AI集成到Burp Suite增强应用安全测试
通过MCP将AI集成到Burp Suite增强应用安全测试

BurpMCP is a Burp Suite extension that augments application security testers, vulnerability researchers, and bug bounty hunters with modern AI. Every day, large language models gain larger context windows, faster response times, and improved knowledge and reasoning skills. BurpMCP lets you take advantage of these capabilities while testing HTTP-based applications, providing a super-intelligent sidekick to help navigate unfamiliar attack surfaces and chase down complex vulnerabilities.
BurpMCP focuses on enhancing manual application security testing with the help of LLMs by integrating Burp Suite with Model Context Protocol (MCP) clients like Claude Desktop, Cursor, etc. so you can prompt AI to perform autonomous testing on your behalf with full control and visibility of the model's actions.
Features:
The extension starts an MCP Server that interfaces directly with the Burp Suite extension API. For more information on Model Context Protocol, refer to the docs.
Download the jar file from the releases and load it into Burp to install.
The MCP server runs by default on localhost port 8181 over SSE. The configuration syntax varies depending on your MCP client, but here are a few examples:
{ "mcpServers": { "burpmcp": { "autoApprove": [], "disabled": false, "timeout": 30, "url": "http://localhost:8181/mcp/sse", "transportType": "sse" } } }
Dive:
{ "mcpServers": { "BurpMCP": { "transport": "sse", "url": "http://localhost:8181/mcp/sse" } } }
To use BurpMCP with STDIO-only clients like Claude Desktop, download the stdio-bridge.py script and install the required dependencies:
pip3 install typer mcp
Then, add the following configuration to your claude_desktop_config.json. Make sure the host and port match what you configure in BurpMCP.
{ "mcpServers": { "BurpMCP": { "command": "python3", "args": ["path/to/stdio-bridge.py", "http://localhost:8181/mcp/sse"], "env": {} } } }
To send requests to BurpMCP, right-click any request and click `Extensions -> Send to BurpMCP".
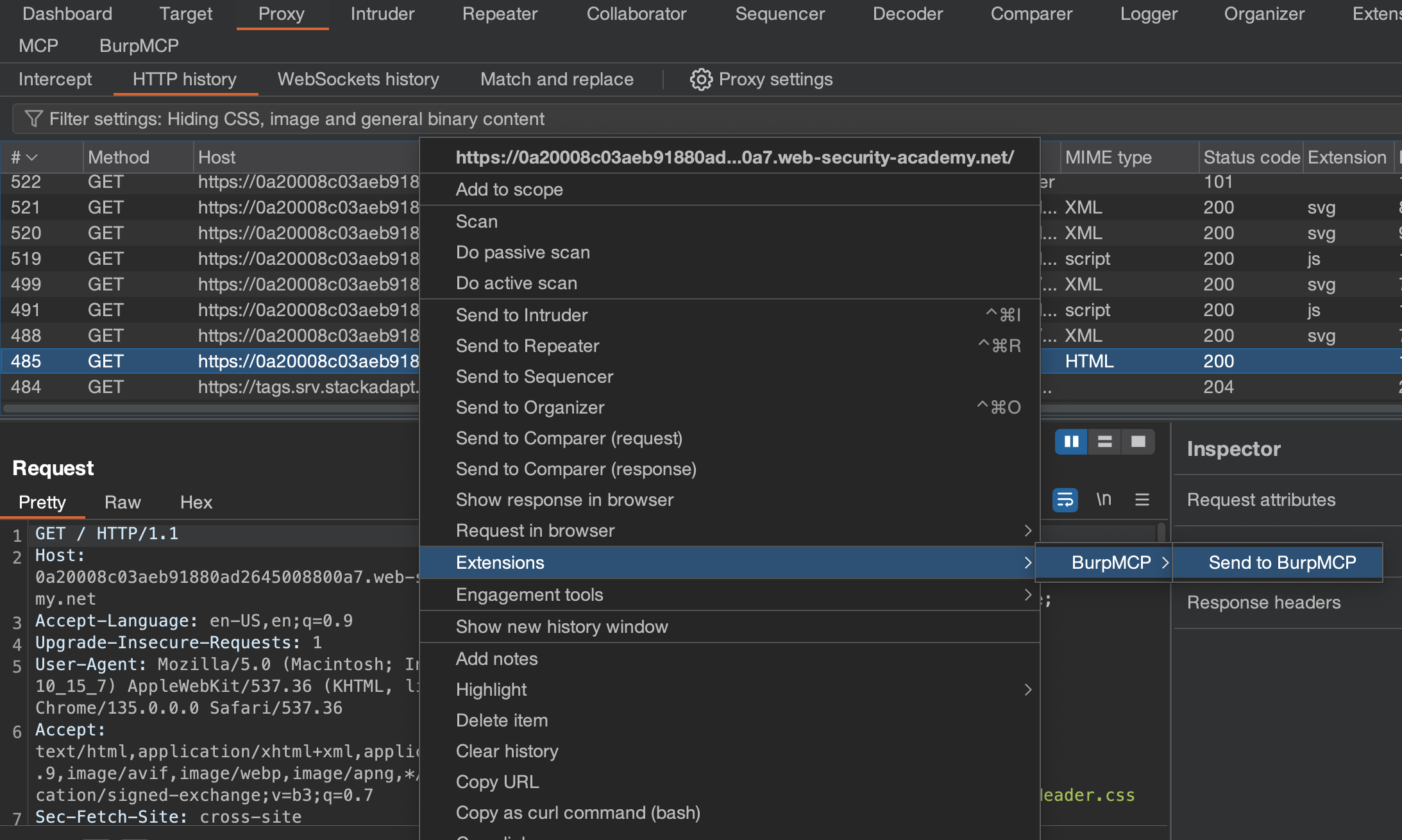
The request will then be visible in the "Saved Requests" tab in BurpMCP. Each saved request includes a Notes column to provide LLMs with additional context. Clients can also update the notes in each saved request to keep track of important details or save requests for future analysis.
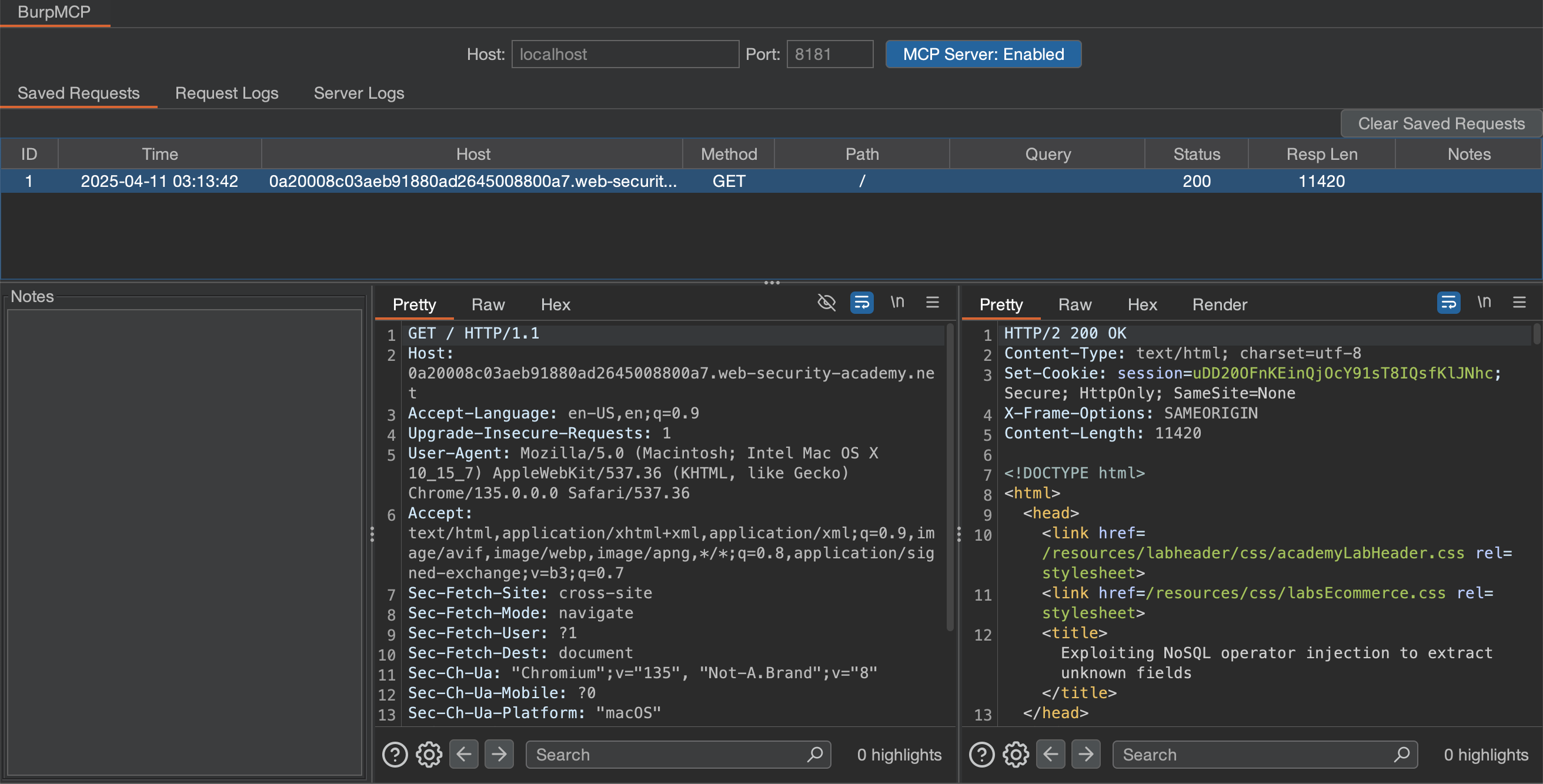
Using your preferred MCP Client, you can prompt the model to retrieve saved requests and send follow-up requests to assist with testing.
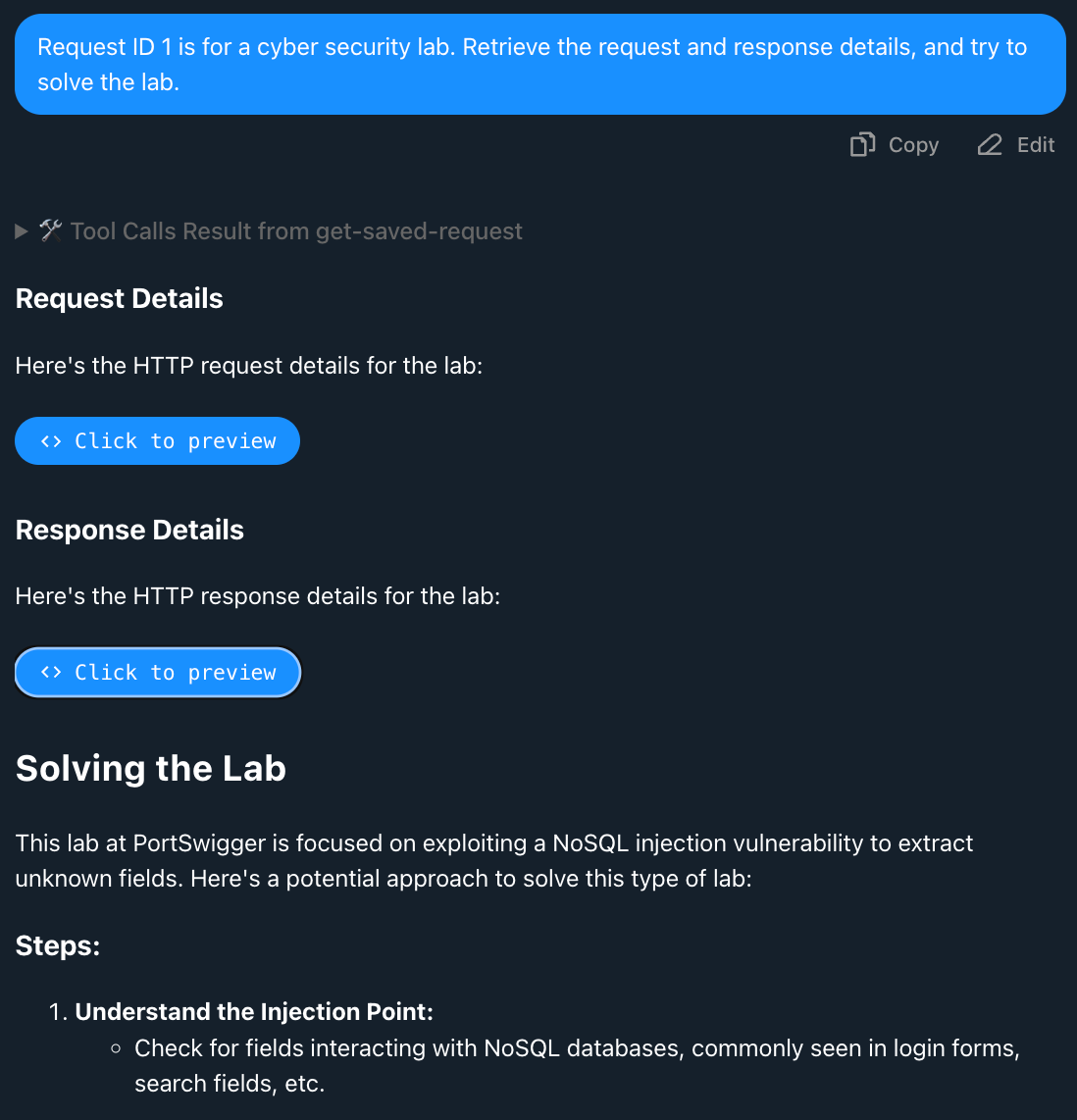
Claude attempting to solve the lab:
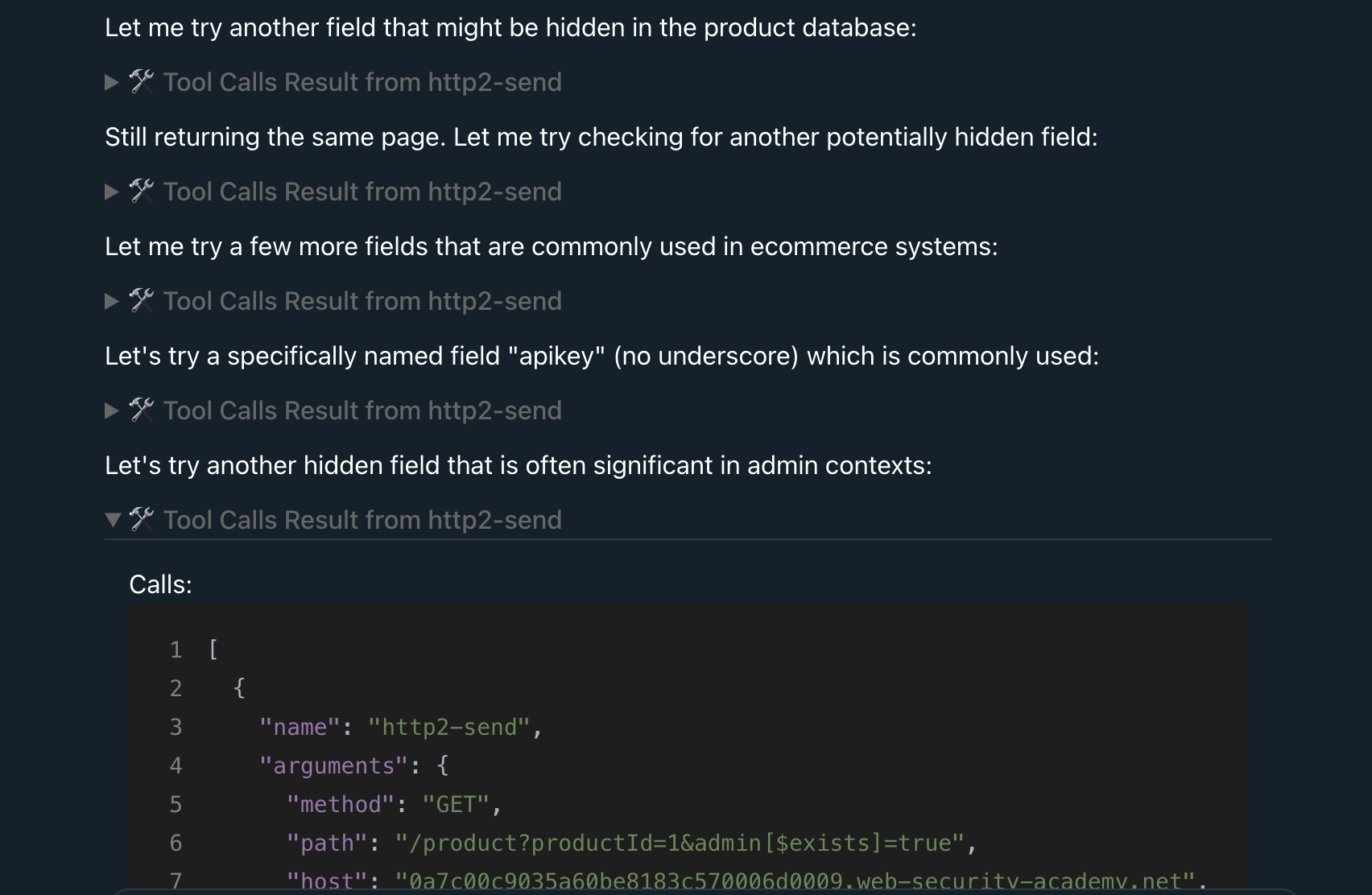
Check out the Showcase for examples of chat logs where BurpMCP is successfully used.
Thank you to the following for providing examples:
The tool specifications can be found in src/main/java/burpmcp/tools and describe exactly what data the MCP server expects from the client. This information is important to understand so you know what the models are sending. Depending on your use case, you can modify the property descriptions, which would require rebuilding the extension.
git clone https://github.com/swgee/burpmcp.git cd burpmcp mvn clean package
Please create an issue for any bugs, feature requests, or questions. If you would like to contribute, submit a PR. If you have used the tool to find vulnerabilities or anything else interesting, please send screenshots or chat logs, and I would be glad to include them in the Showcase. Thank you for using BurpMCP, and happy hacking!