Wazuh
STDIORust-based MCP server bridging Wazuh SIEM system with AI assistants for security data access
Rust-based MCP server bridging Wazuh SIEM system with AI assistants for security data access
A Rust-based server designed to bridge the gap between a Wazuh Security Information and Event Management (SIEM) system and applications requiring contextual security data, specifically tailored for the Claude Desktop Integration using the Model Context Protocol (MCP).
Modern AI assistants like Claude can benefit significantly from real-time context about the user's security environment. The Wazuh MCP Server bridges this gap by providing comprehensive access to Wazuh SIEM data through natural language interactions.
This server transforms complex Wazuh API responses into MCP-compatible format, enabling AI assistants to access:
Rather than requiring manual API calls or complex queries, security teams can now ask natural language questions like "Show me critical vulnerabilities on web servers," "What processes are running on agent 001?" or "Are we meeting PCI-DSS logging requirements?" and receive structured, actionable data from their Wazuh deployment.
This approach is particularly valuable for compliance teams who need to quickly assess security posture, identify gaps in monitoring coverage, validate rule effectiveness, and generate evidence for audit requirements across distributed infrastructure.
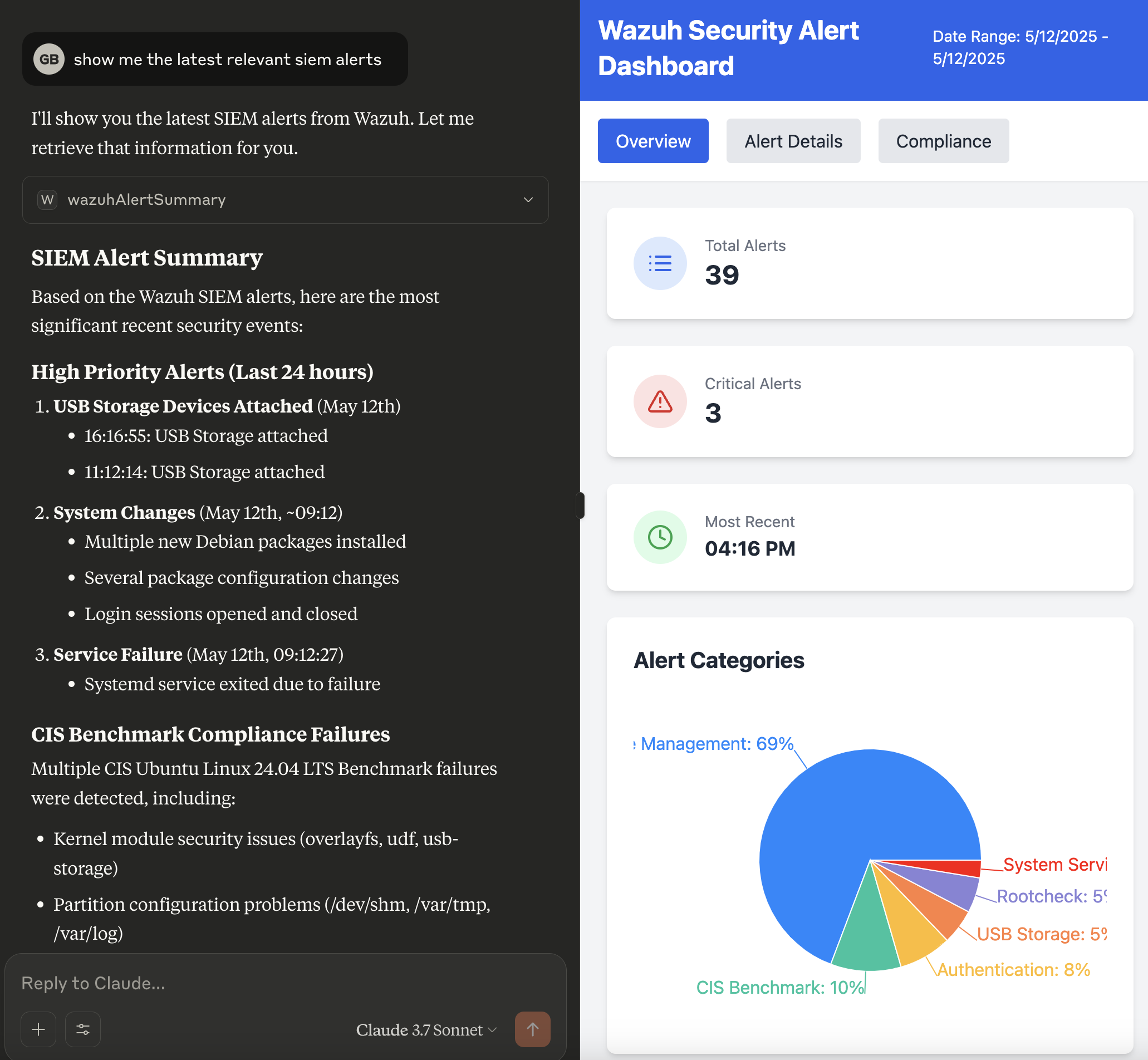
The Wazuh MCP Server provides direct access to Wazuh security data through natural language interactions, enabling several practical use cases:
get_wazuh_alert_summary to quickly identify and prioritize threats requiring immediate attention.get_wazuh_vulnerability_summary and get_wazuh_critical_vulnerabilities to assess security posture of specific agents and prioritize patching efforts.get_wazuh_agent_processes for threat hunting and system analysis.get_wazuh_agent_ports to identify potential attack vectors.get_wazuh_running_agents to ensure comprehensive security coverage.get_wazuh_rules_summary to optimize detection capabilities.get_wazuh_weekly_stats, get_wazuh_remoted_stats, and get_wazuh_log_collector_stats.get_wazuh_cluster_health and get_wazuh_cluster_nodes for operational reliability.search_wazuh_manager_logs and get_wazuh_manager_error_logs for incident investigation.For enhanced threat intelligence capabilities, the Wazuh MCP Server can be combined with the Cortex MCP Server to create a powerful security analysis ecosystem.
Enhanced Capabilities with Cortex Integration:
Example Workflow:
mcp-server-wazuh GitHub repository.mcp-server-wazuh-linux-amd64, mcp-server-wazuh-macos-amd64, mcp-server-wazuh-windows-amd64.exe).chmod +x mcp-server-wazuh-linux-amd64).mcp-server-wazuh and move it to a directory in your system's PATH for easier access.docker pull ghcr.io/gbrigandi/mcp-server-wazuh:latest
Prerequisites:
Build:
git clone https://github.com/gbrigandi/mcp-server-wazuh.git cd mcp-server-wazuh cargo build --release
The binary will be available at target/release/mcp-server-wazuh.
The method for configuring your LLM client will vary depending on the client itself. For clients that support MCP (Model Context Protocol), you will typically need to point the client to the path of the mcp-server-wazuh executable.
Example for Claude Desktop:
Configure your claude_desktop_config.json file:
{ "mcpServers": { "wazuh": { "command": "/path/to/mcp-server-wazuh", "args": [], "env": { "WAZUH_API_HOST": "your_wazuh_manager_api_host", "WAZUH_API_PORT": "55000", "WAZUH_API_USERNAME": "your_wazuh_api_user", "WAZUH_API_PASSWORD": "your_wazuh_api_password", "WAZUH_INDEXER_HOST": "your_wazuh_indexer_host", "WAZUH_INDEXER_PORT": "9200", "WAZUH_INDEXER_USERNAME": "your_wazuh_indexer_user", "WAZUH_INDEXER_PASSWORD": "your_wazuh_indexer_password", "WAZUH_VERIFY_SSL": "false", "WAZUH_TEST_PROTOCOL": "https", "RUST_LOG": "info" } } } }
Replace /path/to/mcp-server-wazuh with the actual path to your binary and configure the environment variables as detailed in the Configuration section.
Once configured, your LLM client should be able to launch and communicate with the mcp-server-wazuh to access Wazuh security data.
If using Docker, create a .env file with your Wazuh configuration:
WAZUH_API_HOST=your_wazuh_manager_api_host WAZUH_API_PORT=55000 WAZUH_API_USERNAME=your_wazuh_api_user WAZUH_API_PASSWORD=your_wazuh_api_password WAZUH_INDEXER_HOST=your_wazuh_indexer_host WAZUH_INDEXER_PORT=9200 WAZUH_INDEXER_USERNAME=your_wazuh_indexer_user WAZUH_INDEXER_PASSWORD=your_wazuh_indexer_password WAZUH_VERIFY_SSL=false WAZUH_TEST_PROTOCOL=https RUST_LOG=info
Configure your claude_desktop_config.json file:
{
"mcpServers": {
"wazuh": {
"command": "docker",
"args": [
"run", "--rm", "-i",
"--env-file", "/path/to/your/.env",
"ghcr.io/gbrigandi/mcp-server-wazuh:latest"
]
}
}
}
Configuration is managed through environment variables. A .env file can be placed in the project root for local development.
| Variable | Description | Default | Required |
|---|---|---|---|
WAZUH_API_HOST | Hostname or IP address of the Wazuh Manager API server. | localhost | Yes |
WAZUH_API_PORT | Port number for the Wazuh Manager API. | 55000 | Yes |
WAZUH_API_USERNAME | Username for Wazuh Manager API authentication. | wazuh | Yes |
WAZUH_API_PASSWORD | Password for Wazuh Manager API authentication. | wazuh | Yes |
WAZUH_INDEXER_HOST | Hostname or IP address of the Wazuh Indexer API server. | localhost | Yes |
WAZUH_INDEXER_PORT | Port number for the Wazuh Indexer API. | 9200 | Yes |
WAZUH_INDEXER_USERNAME | Username for Wazuh Indexer API authentication. | admin | Yes |
WAZUH_INDEXER_PASSWORD | Password for Wazuh Indexer API authentication. | admin | Yes |
WAZUH_VERIFY_SSL | Set to true to verify SSL certificates for Wazuh API and Indexer connections. | false | No |
WAZUH_TEST_PROTOCOL | Protocol for Wazuh connections (e.g., "http", "https"). Overrides client default. | https | No |
RUST_LOG | Log level (e.g., info, debug, trace). | info | No |
Note on WAZUH_VERIFY_SSL: For production environments, it is strongly recommended to set WAZUH_VERIFY_SSL=true and ensure proper certificate validation for both Wazuh Manager API and Wazuh Indexer connections. Setting it to false disables certificate checks, which is insecure.
The "Required: Yes" indicates that these variables are essential for the server to connect to the respective Wazuh components. While defaults are provided, they are unlikely to match a production or non-local setup.
git clone https://github.com/gbrigandi/mcp-server-wazuh.git cd mcp-server-wazuh
cp .env.example .env.env file with your specific Wazuh API details (e.g. WAZUH_API_HOST, WAZUH_API_PORT).cargo build
cargo run # Or use the run script (which might set up stdio mode): # ./run.sh
The server is built using the rmcp framework and facilitates communication between MCP clients (e.g., Claude Desktop, IDE extensions) and the Wazuh MCP Server via stdio transport. The server interacts with the Wazuh Indexer and Wazuh Manager APIs to fetch security alerts and other data.
sequenceDiagram participant ClientApp as Client Application (e.g., IDE Extension / Claude Desktop) participant WazuhMCPServer as Wazuh MCP Server (this application) participant WazuhAPI as Wazuh API ClientApp->>+WazuhMCPServer: (stdio) MCP Initialize WazuhMCPServer-->>-ClientApp: (stdout) MCP Initialized ClientApp->>+WazuhMCPServer: (stdio) MCP Request (tools/list) WazuhMCPServer->>WazuhMCPServer: Parse MCP Request WazuhMCPServer->>WazuhMCPServer: Process internally WazuhMCPServer-->>-ClientApp: (stdout) MCP Response (available tools) ClientApp->>+WazuhMCPServer: (stdio) MCP Request (tools/call for wazuhAlerts) WazuhMCPServer->>WazuhMCPServer: Parse MCP Request WazuhMCPServer->>+WazuhAPI: Request Wazuh Alerts (with WAZUH_USER, WAZUH_PASS) WazuhAPI-->>-WazuhMCPServer: Wazuh Alert Data (JSON) WazuhMCPServer->>WazuhMCPServer: Transform Wazuh Alerts to MCP Format WazuhMCPServer-->>-ClientApp: (stdout) MCP Response (alerts)
Data Flow (stdio focus):
stdin.stdin.WAZUH_USER, WAZUH_PASS).src/mcp/transform.rs) processes each alert, mapping Wazuh fields to MCP fields.stdout.stdout.This stdio interaction allows for tight integration with local development tools or other applications that can manage child processes. An optional HTTP endpoint (/mcp) may also be available for clients that prefer polling.
The server communicates via stdin and stdout using JSON-RPC 2.0 messages, adhering to the Model Context Protocol (MCP).
Example interaction flow:
Client Application (e.g., IDE extension) starts the mcp-server-wazuh process.
Client sends initialize request to server's stdin:
{ "jsonrpc": "2.0", "id": 0, "method": "initialize", "params": { "protocolVersion": "2024-11-05", "capabilities": { "sampling": {}, "roots": { "listChanged": true } }, "clientInfo": { "name": "mcp-inspector", "version": "0.11.0" } } }
Server sends initialize response to client via stdout:
{ "jsonrpc": "2.0", "id": 1, "result": { "protocolVersion": "2024-11-05", "capabilities": { "prompts": {}, "resources": {}, "tools": {} }, "serverInfo": { "name": "rmcp", "version": "0.1.5" }, "instructions": "This server provides tools to interact with a Wazuh SIEM instance for security monitoring and analysis.\nAvailable tools:\n- 'get_wazuh_alert_summary': Retrieves a summary of Wazuh security alerts. Optionally takes 'limit' parameter to control the number of alerts returned (defaults to 100)." } }
Client sends notifications/initialized to server's stdin:
(This is a notification, so id is omitted by the client.)
{ "jsonrpc": "2.0", "method": "notifications/initialized" }
Client requests available tools by sending tools/list to server's stdin:
{ "jsonrpc": "2.0", "id": 1, "method": "tools/list", "params": {} }
Server responds with the list of tools to client via stdout:
{ "jsonrpc": "2.0", "id": 2, "result": { "tools": [ { "name": "get_wazuh_alert_summary", "description": "Retrieves a summary of Wazuh security alerts. Returns formatted alert information including ID, timestamp, and description.", "inputSchema": { "$schema": "http://json-schema.org/draft-07/schema#", "properties": { "limit": { "description": "Maximum number of alerts to retrieve (default: 100)", "format": "uint32", "minimum": 0.0, "type": ["integer", "null"] } }, "title": "GetAlertSummaryParams", "type": "object" } } ] } }
Client calls the get_wazuh_alert_summary tool by sending tools/call to server's stdin:
{ "jsonrpc": "2.0", "id": 3, "method": "tools/call", "params": { "name": "get_wazuh_alert_summary", "arguments": { "limit": 5 } } }
Server receives on stdin, processes the get_wazuh_alert_summary call (which involves querying the Wazuh Indexer API and transforming the data).
Server sends tools/call response with formatted alerts to client via stdout:
{ "jsonrpc": "2.0", "id": 3, "result": { "content": [ { "type": "text", "text": "Alert ID: 1747091815.1212763\nTime: 2024-01-15T10:30:45.123Z\nAgent: web-server-01\nLevel: 7\nDescription: Attached USB Storage" }, { "type": "text", "text": "Alert ID: 1747066333.1207112\nTime: 2024-01-15T10:25:12.456Z\nAgent: database-server\nLevel: 5\nDescription: New dpkg (Debian Package) installed." } ], "isError": false } }
Or, if no alerts are found:
{ "jsonrpc": "2.0", "id": 3, "result": { "content": [ { "type": "text", "text": "No Wazuh alerts found." } ], "isError": false } }
Or, if there's an error connecting to Wazuh:
{ "jsonrpc": "2.0", "id": 3, "result": { "content": [ { "type": "text", "text": "Error retrieving alerts from Wazuh: HTTP request error: connection refused" } ], "isError": true } }
cargo fmt).cargo clippy).httpmock) and a test MCP client.
# Run all tests cargo test # Run specific integration test (example for HTTP tests) # cargo test --test integration_test # Run tests with detailed logging RUST_LOG=debug cargo test
tests/README.md for more details on running tests and using the test client CLI.This project is licensed under the MIT License.