Hydra
STDIOAI-powered pentesting toolkit connecting assistants to security tools via MCP
AI-powered pentesting toolkit connecting assistants to security tools via MCP
⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⠿⠿⠿⠿⠿⢿⣿⣿⣿⣿⣿
⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⠿⣿⣿⠟⠙⠻⠿⠋⠙⠻⠷⠄⠀⠀⠀⠀⠀⠀⢸⣿
⣿⣿⣿⣿⣿⣿⠿⢿⠿⠋⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢠⣾⣿⣿⣿
⣿⣿⣿⣿⣿⡿⠀⠀⠀⠀⠀⢀⣀⣤⣴⣶⣾⣿⣿⣿⣿⣿⣇⡀⠀⠈⠻⠿⣿⣿
⣿⣿⣿⠉⠉⠀⠀⠀⠀⣠⣶⣿⣿⣿⣿⣿⣿⣿⣿⢿⣿⣿⣿⣿⣿⣷⣶⣶⣿⣿
⣿⠿⠟⠀⠀⠀⢀⣠⣾⣿⡿⠻⠿⠟⠙⠿⠟⠻⣿⡆⠈⠻⣿⣿⣿⣿⣿⣿⣿⣿
⣿⠀⠀⠀⠀⢀⣾⠏⠈⠉⠀⠀⠀⠀⠀⠀⠀⠀⠀⠁⠀⠀⠈⠻⣿⣿⣿⣿⣿⣿
⣿⠀⠀⠀⠀⠈⠁⠀⠀⠀⠀⣠⣤⣶⣶⣶⣶⣦⡄⠀⠀⠀⠀⠀⠈⠻⣿⣿⣿⣿
⣿⠀⠀⠀⠀⠀⠀⠀⠀⣠⣾⣿⣿⣿⣿⣿⣿⣿⣦⡀⠀⣾⣿⣿⣆⣤⣾⣿⣿⣿
⣿⠀h⠀⠀⠀⠀⠀⠀⠘⠛⠛⠻⣿⣿⣿⣿⣿⣿⣿⣿⣦⠈⣻⣿⣿⣿⣿⣿⣿⣿
⣿⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠈⠉⢻⣿⣿⡿⠿⠿⠿⢿⣿⣿⣿⣿⣿⣿⣿⣿
⣿⠀⠀⠀⠀⢀⣠⣤⣤⣤⣄⣀⠀⠀⠈⠛⠹⣿⠷⣄⠀⠀⠀⠀⠉⠉⠉⣹⣿⣿
⣿⠀⠀⢀⣾⣿⣿⣿⣿⣿⣿⣿⣷⣤⣀⠀⠀⠀⠀⠀⠀⠀⠀⢀⣴⣶⣶⣿⣿⣿
⣿⠀⢀⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣷⣶⣶⣶⣶⣆⡀⠀⠈⠻⠿⣿⣿⣿
⣿⣤⣼⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣶⣶⣿⣿⣿
A lightweight, extensible cybersecurity toolkit that connects AI assistants to security tools through the Model Context Protocol (MCP), enabling AI-assisted security research, scanning, and analysis.
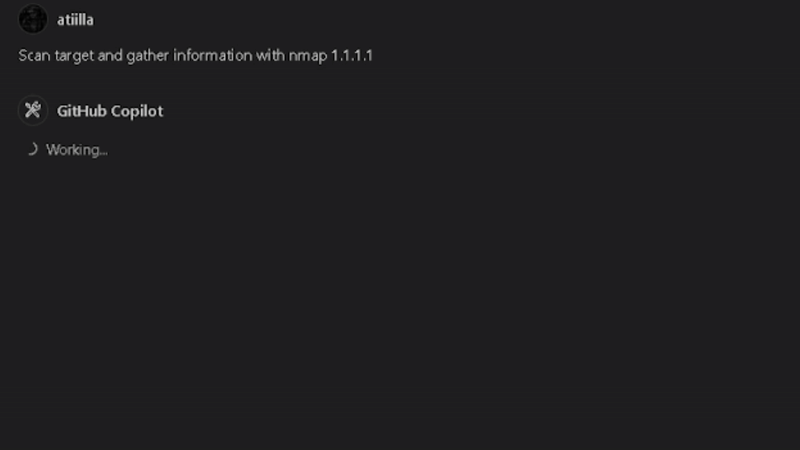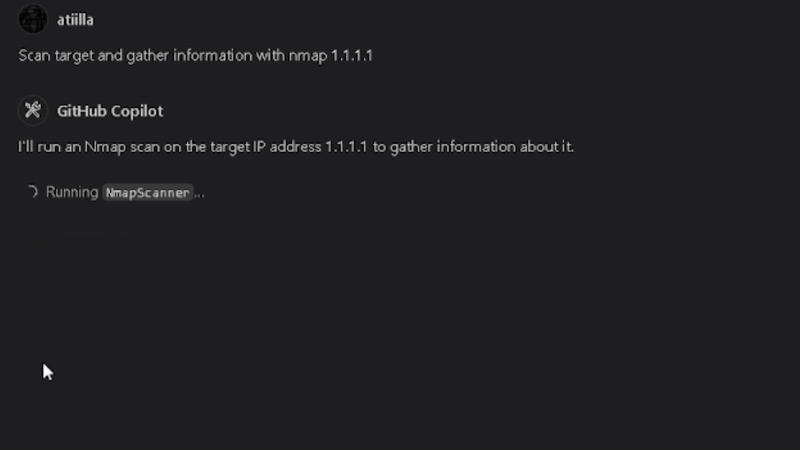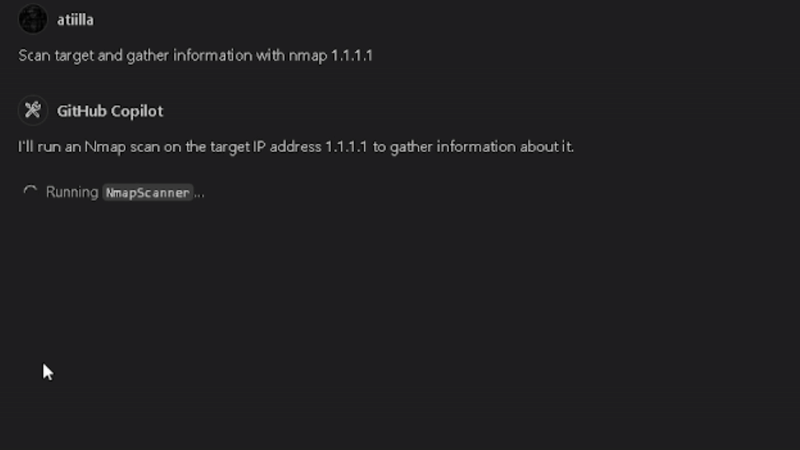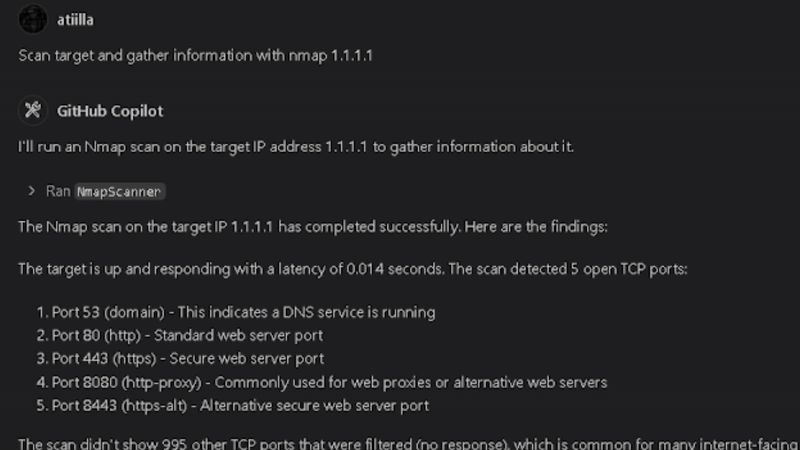
Build te Docker image
git clone https://github.com/happyhackingspace/mcp-hydra.git cd mcp-hydra docker build -t hydramcp .
Edit your claude_desktop_config.json
{ "mcpServers": { "hydramcp": { "command": "docker", "args": ["run", "--rm", "-i","--name","hydramcp", "hydramcp"] } } }
Or Copilot in vscode
mkdir -p .vscode cd .vscode touch mcp.json ```json { "servers": { "hydramcp": { "command": "docker", "args": [ "run", "--rm", "-i", "--net=host", "--privileged", "--name", "hydramcp", "hydramcp" ] } } }
Sublist3r
> Use Sublist3rScanner to find all subdomains for example.com and save results to the "recon" folder.
--
DNSRecon
> Run a DNS reconnaissance scan on example.com using DNSReconScanner with standard scan type.
--
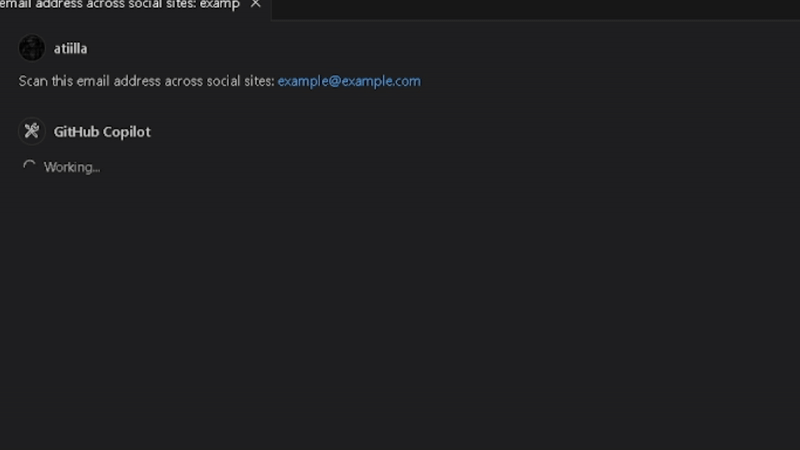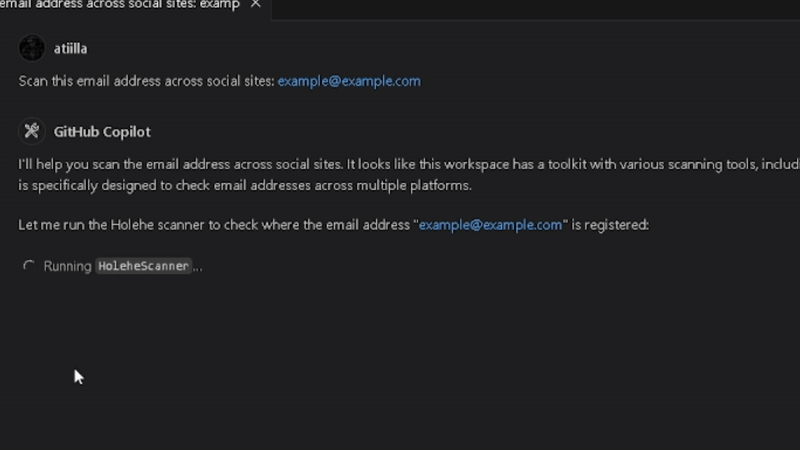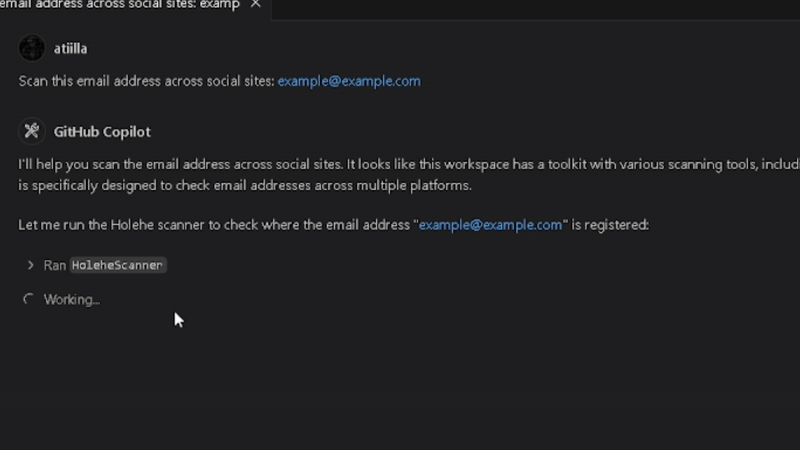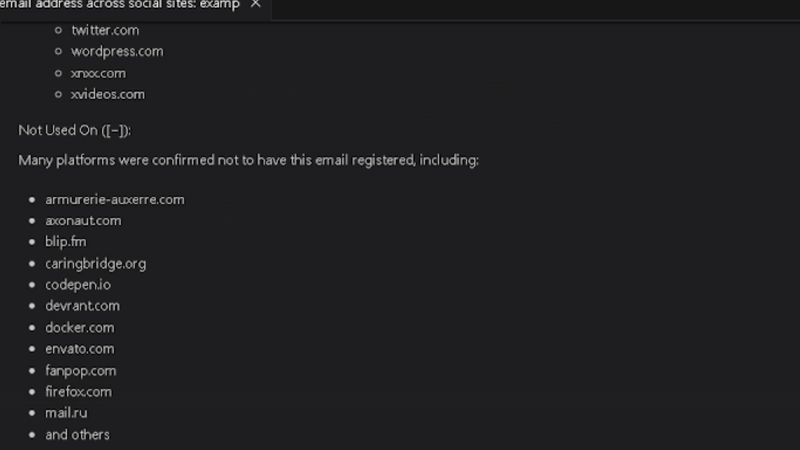
Holehe
> Use HoleheScanner to check if the email address [email protected] is registered on various websites.
--
Nmap
> Scan 192.168.1.1 with NmapScanner to check for open ports in the range 1-1000.
--
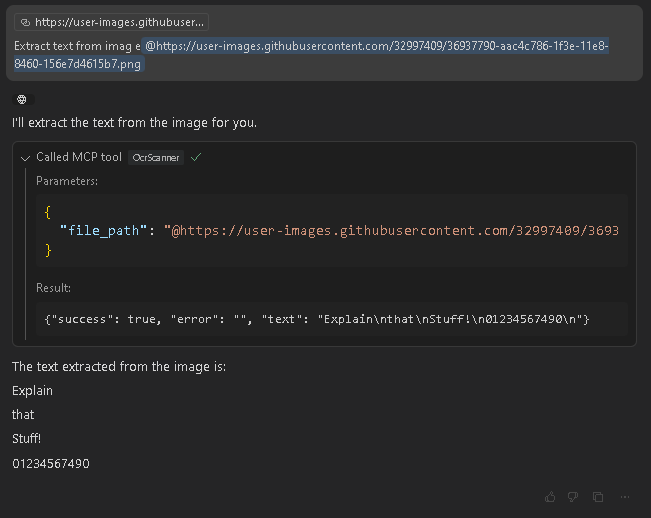
Ocr2Text
> Use OcrScanner to extract text from the screenshot at /path/to/image.png.
--
Sqlmap
> Run SqlmapScanner on http://testphp.vulnweb.com/listproducts.php?cat=1 to check for SQL injection vulnerabilities.
--
WPScan
> Use WPScanScanner to scan the WordPress site at https://example.com for vulnerabilities.
--
Zmap
> Scan the subnet 192.168.1.0/24 for systems with port 80 open using ZmapScanner with 1M bandwidth.
If you want to contribute to this project, please follow these steps:
git checkout -b feature-branch).git commit -m 'Add some feature').git push origin feature-branch).This project is for educational purposes only. Use it at your own risk. The author is not responsible for any damages or legal issues that may arise from the use of this software.