EPSS
STDIOServer for retrieving CVE details with EPSS scores and exploitation likelihood predictions.
Server for retrieving CVE details with EPSS scores and exploitation likelihood predictions.
The EPSS MCP Project is a powerful server designed to retrieve CVE details from the NVD API and fetch EPSS scores from the EPSS server. It provides users with comprehensive vulnerability information, including CVE descriptions, CWEs, CVSS scores, and EPSS percentiles, all in one place.
.env file as NVD_API_KEY)git clone <repository-url> cd epss-mcp-project
It is recommended to use a virtual environment. You can create one using venv or conda. Then, install the required packages:
pip install -r requirements.txt
Create a .env file in the project root and add your NVD API key:
NVD_API_KEY=your-nvd-api-key
To install EPSS Vulnerability Scoring Server for Claude Desktop automatically via Smithery:
npx -y @smithery/cli install @jgamblin/EPSS-MCP --client claude
To start the MCP server locally, run:
python epss_mcp.py
Once the server is running, you can make requests to retrieve CVE details by specifying the CVE ID.
To get details for a specific CVE, use the following format:
GET /cve/<CVE-ID>
Replace <CVE-ID> with the actual CVE identifier (e.g., CVE-2022-1234).
If you want to run the MCP server in Open-WebUI, follow these steps:
To build the Docker container, run:
docker build -t epss_mcp .
Run the container and expose it on port 8000:
docker run -p 8000:8000 epss_mcp
The MCP server will now be accessible at http://localhost:8000.
Below is a screenshot of the MCP server running in the Open-WebUI:
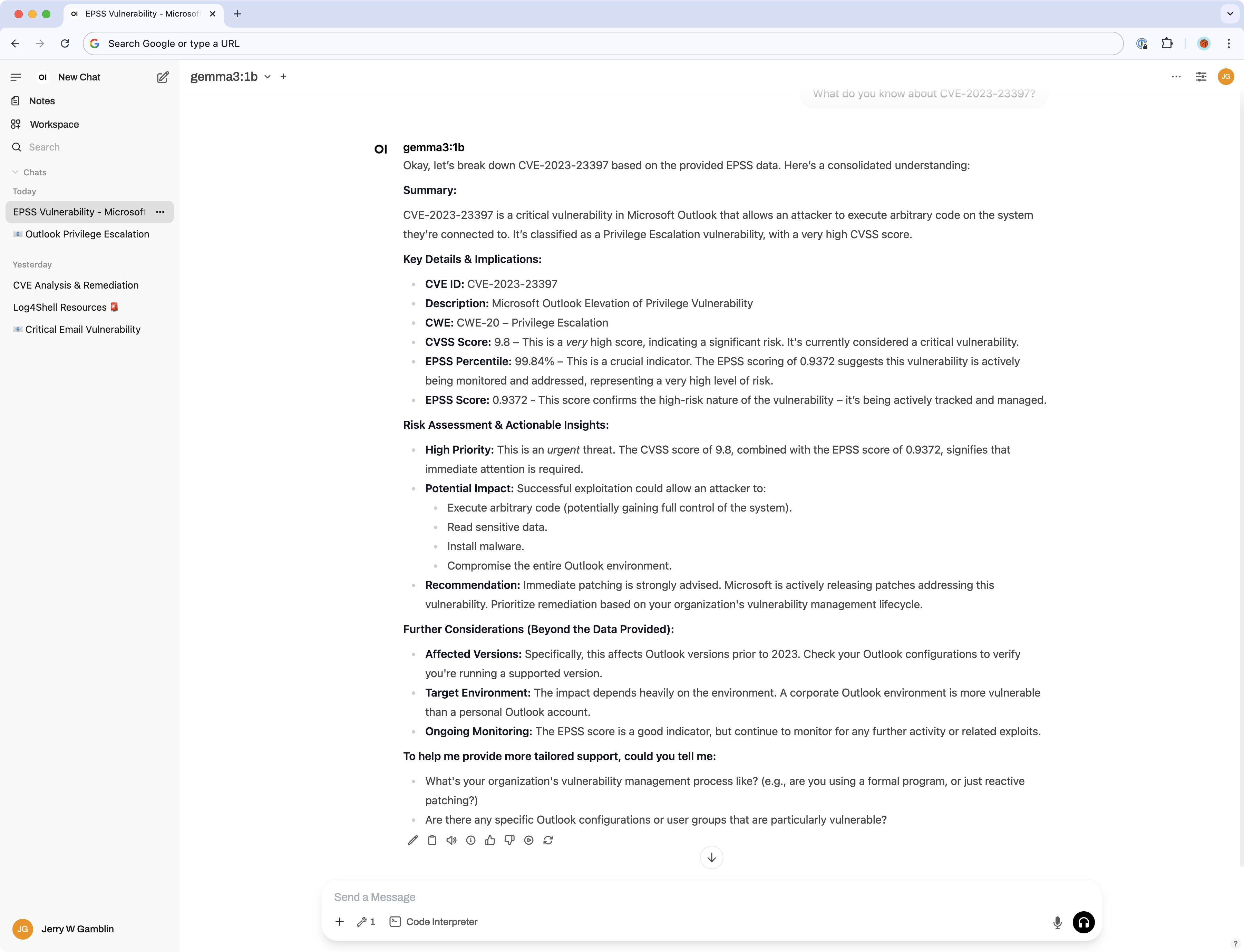
When using the MCP server in Open-WebUI, you can configure the following system prompt to guide interactions:
You are a specialized AI Assistant focused on the Exploit Prediction Scoring System (EPSS). Your expertise lies in delivering and interpreting EPSS data, which includes daily updated probability scores (0-1) and percentiles for Common Vulnerabilities and Exposures (CVEs), indicating the likelihood of their exploitation in the wild within the next 30 days. You are to help cybersecurity professionals understand these predictions, compare them with other metrics like CVSS scores, and use this information to prioritize vulnerability remediation efforts effectively. Provide actionable, data-driven insights in a clear, technically accurate, professional, and solution-oriented manner.
To serve the MCP server to VS Code MCP, follow these steps:
Add the Local Server to VS Code:
Open your VS Code settings.json file and add the following configuration to register the local server:
"mcp.servers": { "EPSS_MCP": { "type": "stdio", "command": "python", "args": [ "/Github/EPSS-MCP/epss_mcp.py" ] } }
Note: Make sure to update the args path to match the location of the epss_mcp.py file on your local machine.
Connect to VS Code:
Start Using the MCP Server: Once connected, VS Code will call the Python file directly to fetch CVE details and EPSS scores.
Below is a screenshot of the MCP server integrated with VS Code:
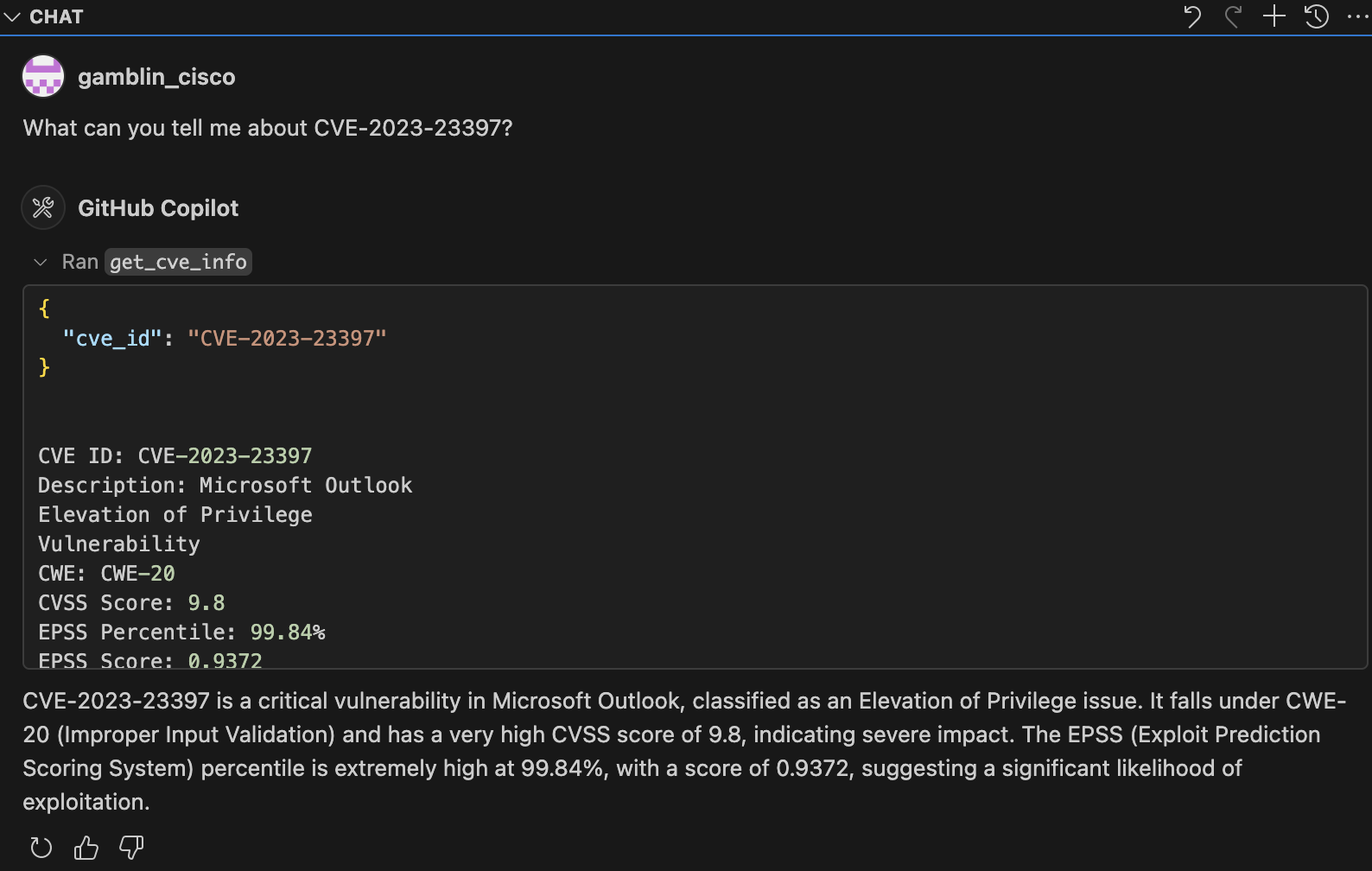
epss-mcp-project
├── epss_mcp.py # Main entry point for the MCP server
├── nvd_api.py # Functions to interact with the NVD API
├── epss_api.py # Functions to interact with the EPSS API
├── epss_mcp_test.py # Test script for the MCP server
├── requirements.txt # Project dependencies
├── Dockerfile # Docker configuration
├── .env # Environment variables (e.g., API keys)
└── README.md # Project documentation
Contributions are welcome! Please feel free to submit a pull request or open an issue for any enhancements or bug fixes.
This project is licensed under the MIT License. See the LICENSE file for more details.