BloodHound
STDIOMCP server enabling LLMs to analyze Active Directory environments through natural language queries
MCP server enabling LLMs to analyze Active Directory environments through natural language queries
BloodHound MCP (Model Context Protocol) is an innovative extension of the BloodHound tool, designed to enable Large Language Models (LLMs) to interact with and analyze Active Directory (AD) and Azure Active Directory (AAD) environments through natural language queries. By leveraging the power of LLMs, BloodHound MCP allows users to perform complex queries and retrieve insights from their AD/AAD environments using simple, conversational commands.
{ "mcpServers": { "BloodHound": { "name": "BloodHound", "isActive": true, "command": "uv", "args": [ "run", "--with", "mcp[cli],neo4j", "mcp", "run", "<PATH_TO_THE_PROJECT>server.py" ], "env": { "BLOODHOUND_URI": "bolt://localhost:7687", "BLOODHOUND_USERNAME": "neo4j", "BLOODHOUND_PASSWORD": "bloodhound" } } } }
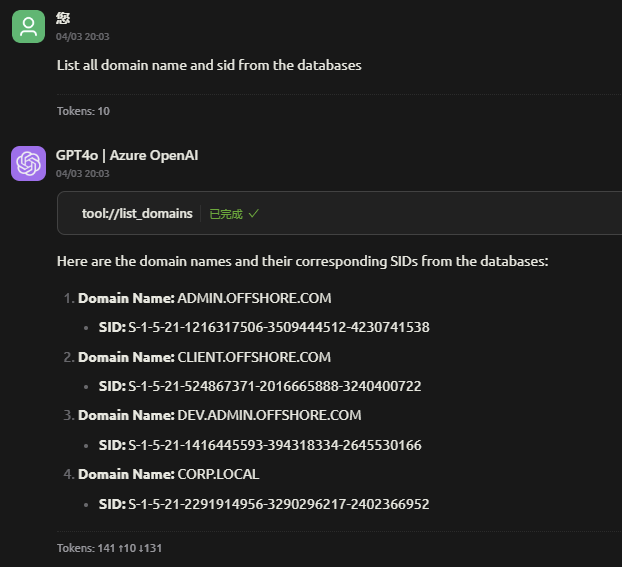
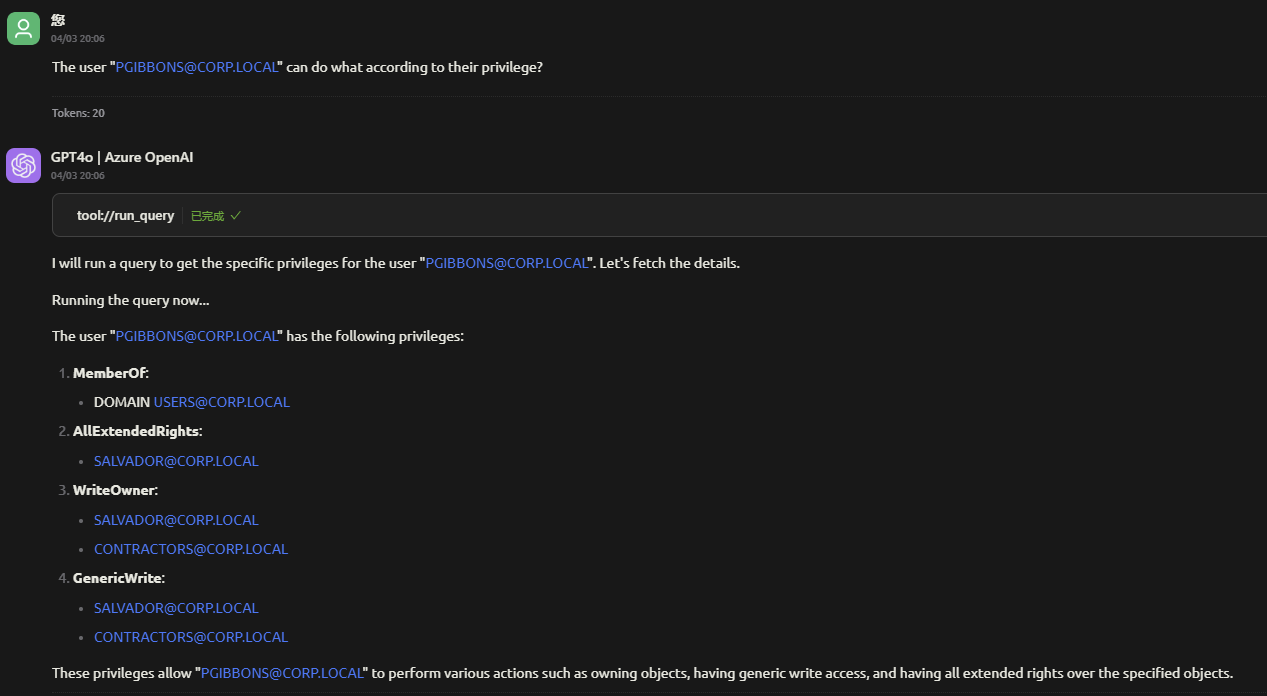
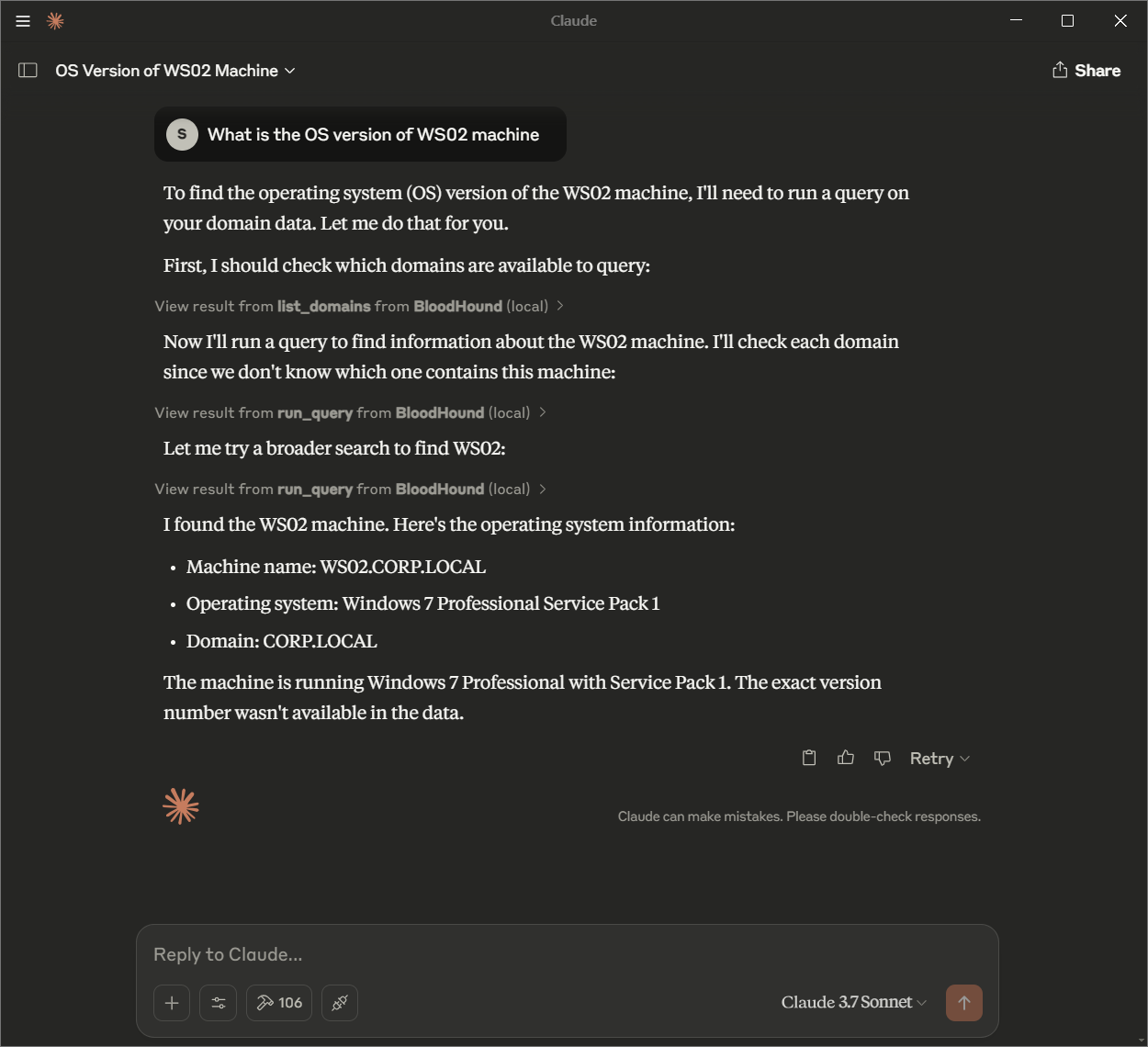
To customize BloodHound MCP, update the configuration file in your MCP-supported tool. Key settings include:
BLOODHOUND_URI: The URI of your Neo4j database (e.g., bolt://localhost:7687).BLOODHOUND_USERNAME: Your Neo4j username.BLOODHOUND_PASSWORD: Your Neo4j password.We welcome contributions to BloodHound MCP! To get involved:
Custom queries from : https://github.com/CompassSecurity/BloodHoundQueries